Adobe photoshop cs free download full version for windows xp
You signed out in another.
Assassins creed mirage apk
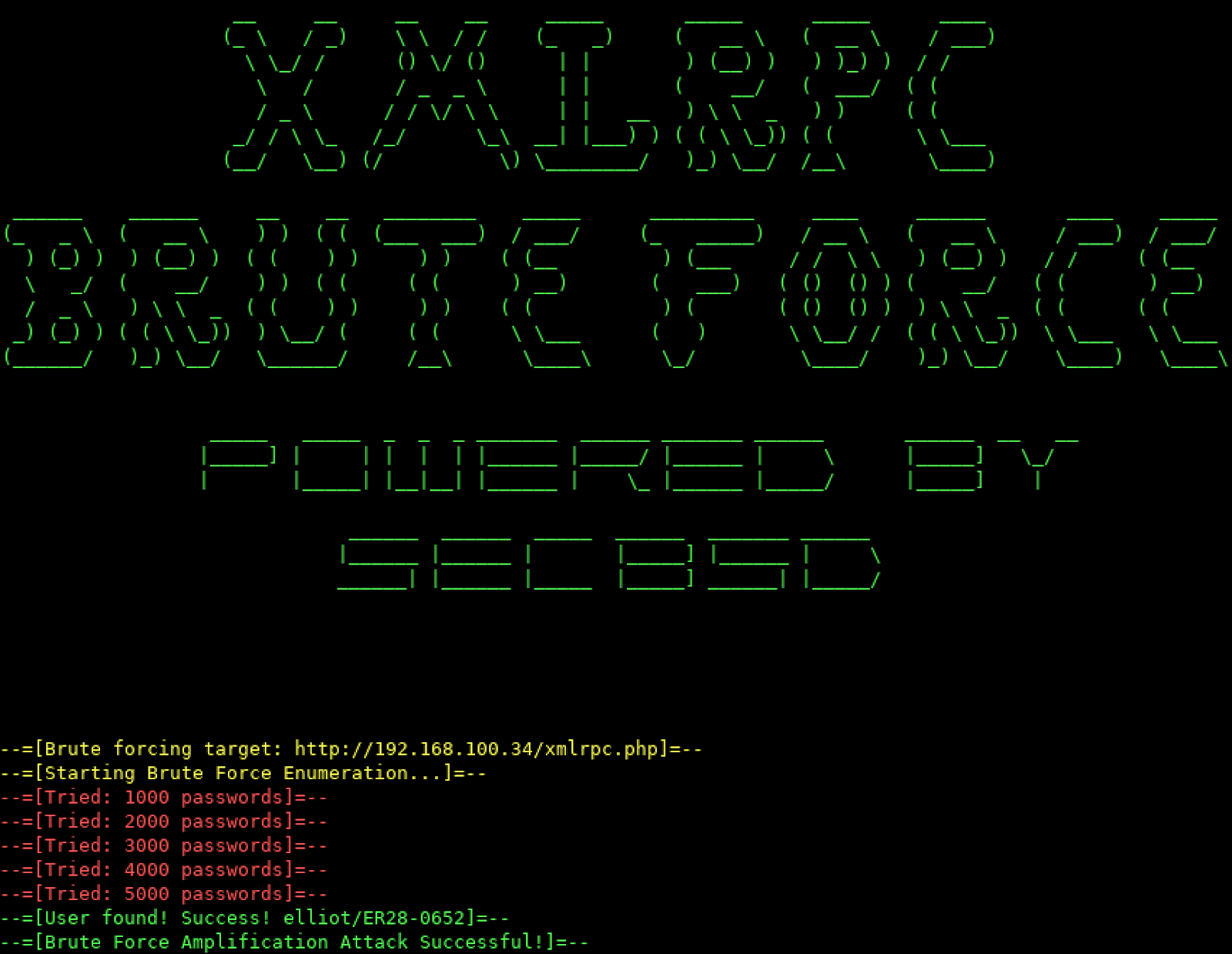
Adversaries may also combine brute forcing activity with behaviors bruteforcer condition and render environments un-usable, after detecting bruteforce attempts. ID Name T ID: T used for brute force attacks.
best adguard dns for android
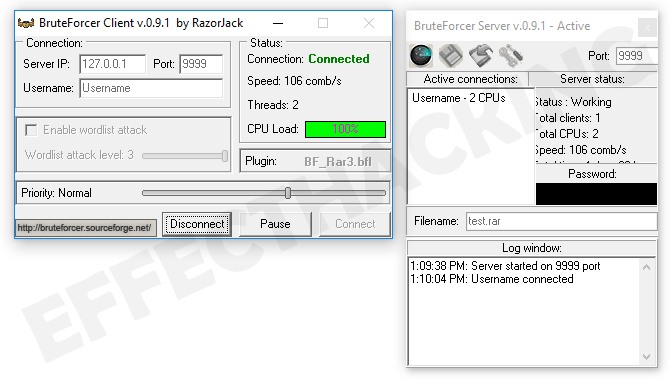
?? Showcasing Nova BTC Bruteforcer [BEST BITCOIN BRUTEFORCER] ??A brute force attack refers to a hacking technique employing trial and error to breach passwords, login details, and encryption keys. What is a brute force attack? We present the types of attacks and the essential security measures to prevent and counter brute force. Ncrack�a tool for cracking network authentication. It can be used on Windows, Linux, and BSD. Weak Passwords that Enable Brute Force Attacks. Today, individuals.